Latest News
Read all latest blog posts

NBD: A Powerful Tool for data center
NBD: A Powerful Tool for data center NBD, the abbreviation for Network Block Device (protocol), is a protocol that was initially implemented in the Linux kernel version 2.
Read More
Avoiding Single-Point-of-Failure and securing the Root Infrastructure: TCG TPM 2.0
What is TCG TPM 2.0? Trusted Computing Group (TCG) Trusted Platform Module (TPM) 2.
Read More
Demystifiying SMPC (Secure multi-party computation) and its threat model
Prologue SMPC is an interesting topic, whose the applications include systematic security and cryptographic engineering, and this article will discuss its principles, threat models and use-case.
Read More
The exploit recon 'msg_msg' and its mitigation in VED
Why msg_msg? The size of structure is control by userspace Firstly, the length of the msg_msg struct can be indirectly controlled from userspace, which means that msg can overlap the cache of the specified types.
Read More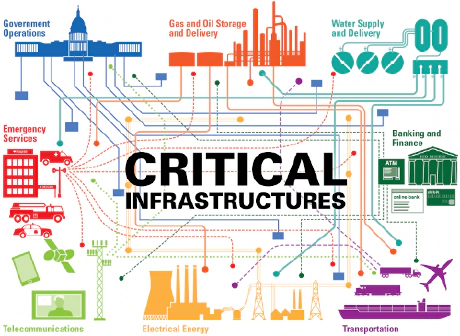
The below-OS for supply chain of critical infrastructure protection
Background The endless cyber “war” in the levels of OS
Read More
What can we learn from leaked Insyde's BIOS for Intel Alder Lake
Leaked story timeline According to the timestamp of the github repository, an unidentified user uploaded the Insyde’s partial firmware solution (4.
Read More
The magic about how modern OS boot
Linux kernel Under x86/amd64 architecture, Linux kernel is usually packed into bzImage format, which contains a partially-filled data structure for boot parameter, and multiple entry points of stages for 16-bit real mode, 32-bit protected mode, and 64-bit long mode if built for amd64, the last stage is a self-decompressing flat binary, which will decompress and execute the gzip-compressed kernel image proper, also in the format of flat binary, stored in its data segment.
Read More
Technical analysis of syzkaller based fuzzers: It's not about VaultFuzzer!
0. VaultFuzzer S0rry, VaultFuzzer is not the main player today. We’re going have little ride with Harbian-QA and GREBE today.
Read More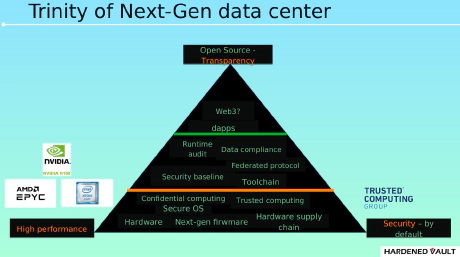
Next Generation Data Center Security: The Cornerstone of Web3?
0. Next generation data center What is the next generation data center?
Read More
VaultBoot: Attestation as a Service
VaultBoot In the highest level of security profile (CRITICAL), the Vault 111 hardware node enables multi-trust anchors through the chip security features.
Read More