Welcome to HardenedVault
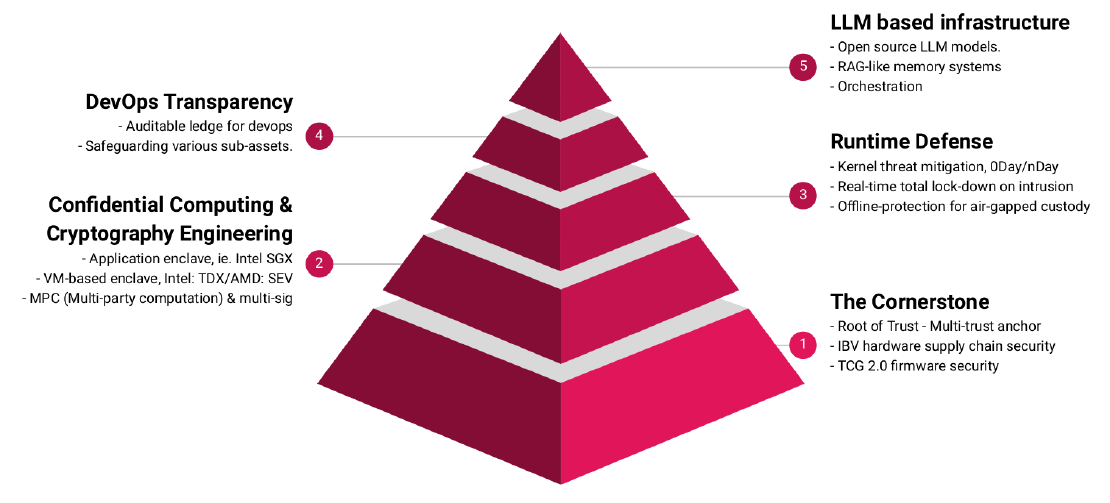
HardenedVault spent nine years on system-level security technology development. This advanced security technology development has led to increased protection against system tampering. The direct impact, now people can enjoy a Tier-4 level of security on either home computing node or the heavy node in the data center. HardenedVault’s security technologies covers the entire first half of the system security. Starting from the boot process at node level, the root-of-trust is anchored in multiple hardware components, and the chain of trust extends from firmware, operating system to applications. Crucial part of each component follows rigorous compliance/regulation requirements. Integrated with modern mitigation and access control, our security stack is able to defend against the known and unknown vulnerability and exploit vectors by integrating the. Additionally, although standard secured communication guarantees confidentiality and integrity, it is not robust enough to defend against advanced threats against privacy. HardenedVault’s ZKP-based secure communication protocol with metadata protection (to protect machine’s privacy) and deniability to help the customer to build their own decentralized data center/cloud.
Who we are?
Our technical team are a group of old-school hackers, cypherpunks, and stubborn engineers while our management team are originaly from Top 500 C-Level veterans who have spent decades tweaking around interesting things in their respective fields until 2021 when we felt we could do more for the industry, so here we are now.
Our mission
Thanks for visiting the our website. If you’re still reading, it’s likely that you’re a person who is not happy about the current situation of the technology industry. Our vision is simple: to help users build their own Cyber Bunker at the infrastructure level. Achieving this goal requires high performance, security and transparency (open source) that takes into account the industry compliance, as well as decentralization (it’s federated protocol actually) in communications. If you share our philosophical idea, please work with us to make it.