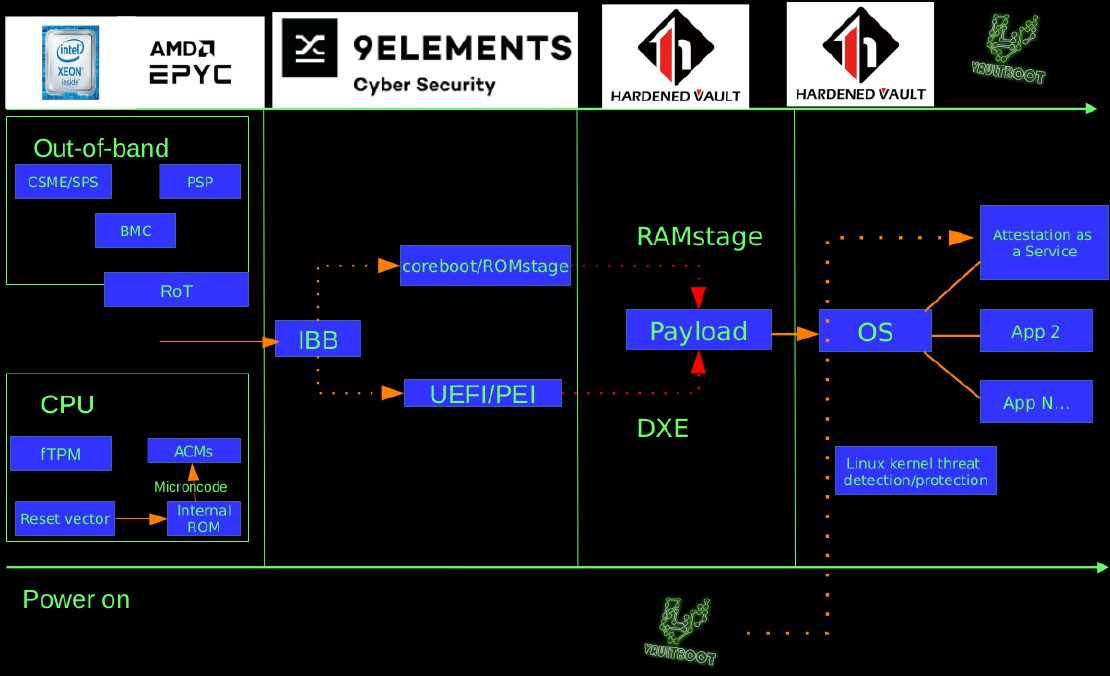
Security as a Service - ATP (Advanced Threat Protection)
CaaS (Compliance as a Service) provides the solution that is easy to compliance (PCI-DSS, GDPR, etc). HaaS (Hardening as a Service) brings security best-practice by default. AaaS (Attestation as a Service) enable the client’s production in full-spectrum mode by both remote and local attestation via TPMv2.0/TXT/SGX and vTPM implementations.
Hardened Linux (Ubuntu 24.04 LTS) for x86_64
$0.05 /hourBeyond compliance
- Security baseline base on CIS/STIG
- VED-LTS (Vault Exploit Defense), for Linux kernel runtime protection. This feature is designed to protect your digital assets from advanced threats such as 0-day Linux kernel exploits, privilege escalation, container escape, and rootkits.
- AppArmor for mandatory access control
- AIDE for file integrity protection
- DNSCrypt-proxy, supporting DNSCrypt relays, local DNS-over-HTTPS, and more
- etc
Hardened Linux (Ubuntu 22.04) for arm64
$0.021 /hourBeyond compliance
- CIS/STIG for compliance
- VED (Linux kernel threat mitigation)
- AppArmor for mandatory access control
- AIDE for file integrity protection
- etc
Hardened Linux (Ubuntu 22.04) for x86_64
$0.05 /hourBeyond compliance
- CIS/STIG for compliance
- SIEM/XDR integration (Wazuh agent)
- VED (Linux kernel threat mitigation)
- AppArmor for mandatory access control
- AIDE for file integrity protection
- etc
Attestation server
$?? /hourEVM (Ephemeral Virtual Machine)
- All features of Beyond compliance
- …
- …
- …
- …
Need a larger plan?
If you plan to deploy our SaaS solution or you need to do the security provionsing (chipset security features, CBnT, TPM/FDE, SGX, TDX/SEV, etc) for the hardware, feel free to ping us. We provide full-stack solution for platform and infrastrcuture security, including GNU/Linux server security, Linux kernel hardening, firmware security, trusted/confidential computing, cryptography engineering and supply chain security of OEM.
Contact Us