The below-OS for supply chain of critical infrastructure protection
Background
The endless cyber “war” in the levels of OS (Operating system) and below-OS didn’t draw the general public’s attentions since 2000s. The disclosure of Stuxnet has made the industry begin to pay attention to OS security. Speaking of BIOS/firmware’s bootkits, it’s getting some attentions until recently for two reasons. The number of public known vulnerablities has been growing:
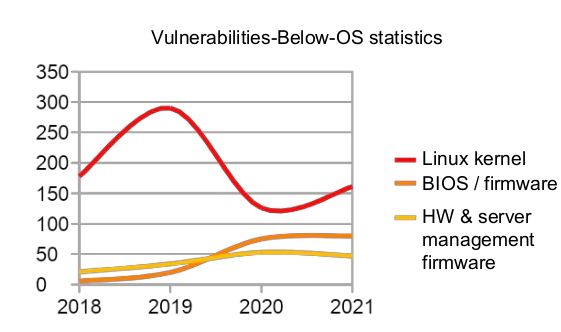
which makes the offensive side having more options to build their weaponized bootkits or buying the off-the-shelf bootkits in underground sites, e.g: an ESP-based bootkits for Windows machine only cost 5k USD plus 200 USD for each rebuild and maybe there are some cheaper implementation you could find:

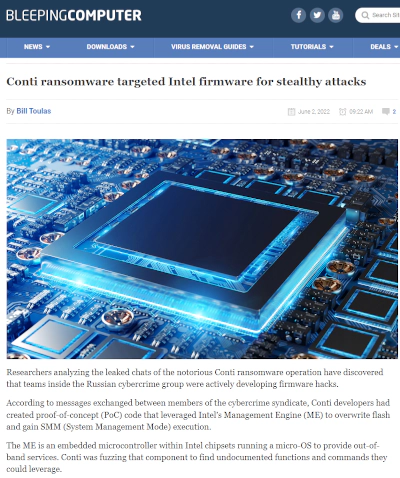
On the other hand, the famous RaaS (Ransomware as a Service) organization, Conti group’s internal chat leaked earlier in this year and Conti group mentioned that they’ve been targeting wider firmwares other than UEFI/SMM and Intel CSME is on their radar as well.
This article will discuss about how US/EU/China treat OS/below-OS techniques from government/regulation perspective.
USA - the ignition of VBOS
Firmware is a special software running on the privilege higher than OS:
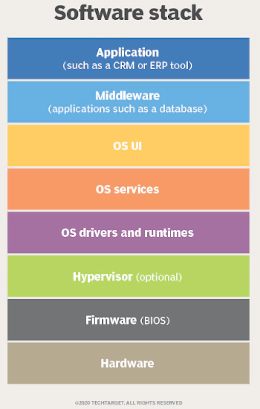
NIST has done a series of special publications:
- Apr 2011, NIST SP 800-147:BIOS Protection Guidelines
- Dec 2011, NIST SP 800-155:BIOS Integrity Measurement Guidelines
- Aug 2014, NIST SP 800-147B:BIOS Protection Guidelines for Servers
- May 2018, NIST SP 800-193:Platform Firmware Resiliency Guidelines
May 26, 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced a campaign VBOS (Vulnerability below the OS in response to EO 14028 on supply chain security, which aims to promote security protection. The offensive and defensive sides have been busy with their game for profit (and for fun?) at the firmware level in the past 15 years but the general public barely know their existence. The VBOS compaign is the first time dragging this “covert warfare” on the table.
February 23, 2022, U.S. DEPARTMENT OF COMMERCE and U.S. DEPARTMENT OF HOMELAND SECURITY released a 97-page report ASSESSMENT OF THE CRITICAL SUPPLY CHAINS SUPPORTING THE U.S. INFORMATION AND COMMUNICATIONS TECHNOLOGY INDUSTRY in response to EO14017, which directly stated that firmware is the weakest link, and the U.S. government has severely warned that firmware security is a high-risk area for “single point of failure”, the report talks about complex supply chains and attacker advantages that pose a significant risk to users.
Germany
Although there is no systematic firmware security publication like what NIST does in the United States, the German Federal Office for Information Security (BSI) has repeatedly and publicly mentioned “open firmware support and follow-up”. In 2019, BSI certified the network security products of Genua GmbH, a veteran German security firm (BSI-DSZ-CC-1085-2019), which supports the open-source firmware to implement firmware security features. In October 2021, the European Commission started the legislative process for mandatory firmware security updates for the consumer market, while NIS2 and RCE at EU level in the law on the protection of critical infrastructure were extended to KRITIS at the German national level(ITSIG 2.0) which mandates that the vendor must provide long-term maintenance for the firmware and critical infrastructure operator must patch the firmware as other softwares.
China
China adopted the regulations on the Security Protection of Critical Information Infrastructure on April 27, 2021, which came into effect on September 1, 2021. It’s clearly defines the scope of critical information infrastructure as “public communications and information services, energy, transportation, water plant, finanical sector, public services, e-government, national defense science and technology industry and other important industries and fields”. One year after, the detail of technical requirement has been issued in a national standard Information security technology -Cybersecurity requirements for critical information infrastructure protection, although it does not directly mention the technical risks and protection requirements about OS and below-OS, it points out these two important components of advanced protection as part of technical implementation’s goal:


Hong Kong SAR
Critical infrastrucutre cyber security protection is still in progress and yet we don’t have any public information.
Wrap-up
It can be seen that the way on which governments in China, Germany and the United States promote the security of critical infrastructure supply chains are different. United States has centered on technical guideline as options since EO 14028, which provides a fair amount of reference to ease the process of technical assessment and operations for the enterprise and government organization. EU has set minimum technical requirements as mandatory compliance, but considering other compliance factors such as GDPR as risk-base approach, which will push little harder on the companies that do not meet the level of industry best practices actually bring higher compliance risks. China’s strategy is different from the United States and Europe. The Cybersecurity requirements for critical information infrastructure protection defines both technical scopes and objectives, and other technical guidelines should be used as complement materials to specific technology. Countries such as Japan, Singapore, and South Korea also have corresponding compliance and technical guidelines for critical infrastructure protection, which are beyond the scope of this article.
Avanced threat protection is a global trend which is inevitable. Platform firmware is one of the core components in the system and more importantly (to CISO) it’s going to be part of future compliance. CISOs should spend a little time on OS and below-OS by taking off the burden of application and perimeter security for a moment. Some industries not relying on compliance-driven such as crypto Custody/Exchange, might require a more “radical” strategy to welcome the desert of the real.
Vault Labs’s work
- Secure Firmware Development Best Practices v1.1
https://ogi-cdn.s3.us-east-2.amazonaws.com/csis/firmware-security-best-practices-v1.1.pdf
- What every CISO and security engineer should know about Intel CSME
https://hardenedvault.net/blog/2021-07-16-ciso-seceng_csme/
- VaultBoot
https://github.com/hardenedvault/vaultboot
- Firmware security technical guideline - OSFF (Open Source Firmware Foundation)
(still in progress)
- 摘要:基础架构安全弹性技术指南草案(固件安全篇)
https://hardenedvault.net/zh-cn/blog/2022-05-19-fw-guideline/
- VaultBoot: Attestation as a Service
https://hardenedvault.net/blog/2022-06-27-vaultboot-attestation/