Latest News
Read all latest blog posts

VED 2026: after CFI - data only
after CFI - data only The exploitation techniques and mitigation has been evolving rapidly since the paper “Smash the Stack for Fun and Profit” released in Phrack Issue 49.
Read More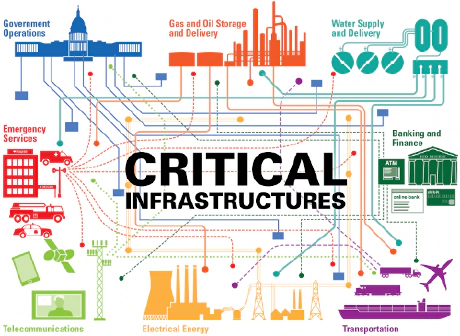
The below-OS for supply chain of critical infrastructure protection
Background The endless cyber “war” in the levels of OS
Read More
What can we learn from leaked Insyde's BIOS for Intel Alder Lake
Leaked story timeline According to the timestamp of the github repository, an unidentified user uploaded the Insyde’s partial firmware solution (4.
Read More
The magic about how modern OS boot
Linux kernel Under x86/amd64 architecture, Linux kernel is usually packed into bzImage format, which contains a partially-filled data structure for boot parameter, and multiple entry points of stages for 16-bit real mode, 32-bit protected mode, and 64-bit long mode if built for amd64, the last stage is a self-decompressing flat binary, which will decompress and execute the gzip-compressed kernel image proper, also in the format of flat binary, stored in its data segment.
Read More
Technical analysis of syzkaller based fuzzers: It's not about VaultFuzzer!
0. VaultFuzzer S0rry, VaultFuzzer is not the main player today. We’re going have little ride with Harbian-QA and GREBE today.
Read More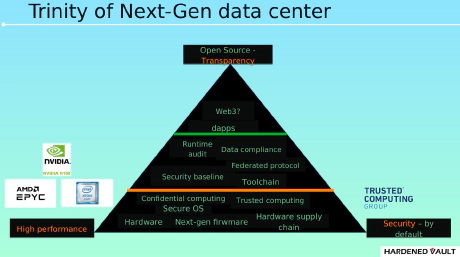
Next Generation Data Center Security: The Cornerstone of Web3?
0. Next generation data center What is the next generation data center?
Read More
VaultBoot: Attestation as a Service
VaultBoot In the highest level of security profile (CRITICAL), the Vault 111 hardware node enables multi-trust anchors through the chip security features.
Read More
VED (Vault Exploit Defense): Open source implementation
VED - Linux kernel threat detection and prevention system LKM version of VED goes public finally.
Read More
Tetragon: case study of security product's self-protection
Story background CTO of cloud-native security company Isovalent announced that their eBPF-based Security Observability and Runtime Enforcement solution Tetragon ( WayBackMachine 20220516 ) become open source after years of development in May 16 2022.
Read More
Exploiting CVE-2021-26708 (Linux kernel) with sshd
Kernel vulnerability CVE-2021-26708 Alexander Popov has published an article Four Bytes of Power: Exploiting CVE-2021-26708 in the Linux kernel which use a four-byte overwrite vulnerability to do privilege escalation.
Read More