Vault Range - The Measure and Resilience of Weaponized Exploit Methods for Linux
Disclaimer
VED (Vault Exploit Defense) test image contains only the VED kernel module, and does not contain any security baselines, access control policies and situational hardening solution. This image is for testing only and HardenedVault Limited do not responsible for any risks posed by any use in the production environment.
Background
HardenedVault has received some feedback after the release of the VED Technical Whitepaper. In order to further communicate and answer questions, HardenedVault decided to release a test image showing the exploit methodology.
What is the Digital Arms Industry
The digital arms industry involves the use of computer technology and network penetration techniques to build and sell tools, programs, and services that are used to attack and compromise information systems such as computing devices, networks, and software. These tools and services also include exploit tools, remote access software, trojans, phishing and hacking techniques, which are targeted to steal sensitive information, control or destroy target systems. The users of digital arms may include government military and intelligence agencies, criminal gangs, and hacker groups. 0-day exploit is an important part of the digital arms industry, you can refer to Maor Shwartz’s article for more information about the 0-day industry and the trends of the digital arms industry. People like Drebin have counterparts in the digital arms industry all over the world.

Exploit Stage
In our previous write-up, we mentioned that detection of the exploit process can be done in three stages. The earlier the stage the more efficient the detection would be, but unfortunately, except for a few defense mechanisms (such as PaX KERNSEAL) that can detect in the pre-exploitation stage, most of the defense mechanisms work in the Exploitation stage and Post-exploitation stage. VED can implement detection and blocking earlier in some specific exploit methods, but for the most part, it only works in the exploitation and post-exploitation stage typically.
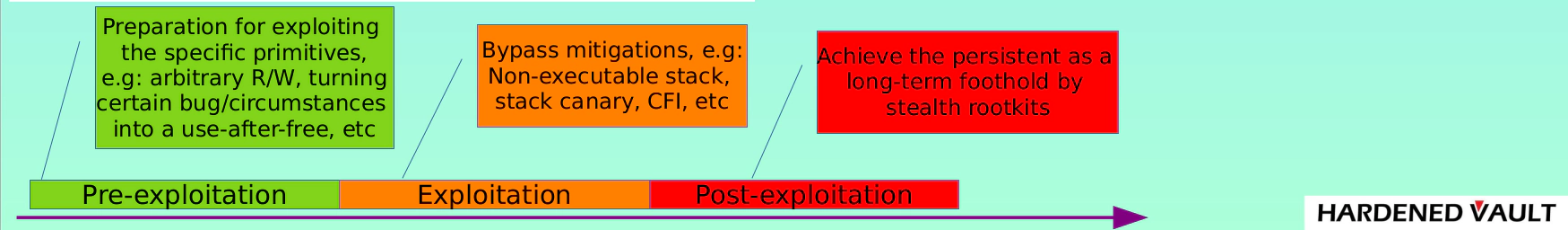
Exploit Method
Vault Exploits Defense (VED) is a runtime threat detection and defense solution for the Linux kernel that can detect and block known (N-day) and unknown (0-day) Linux kernel exploits. These exploits are often extremely dangerous and difficult to detect. It is important to note that VED detects and defends against exploit methods, rather than hard-coding defenses for specific vulnerabilities.
Exploit Test Image
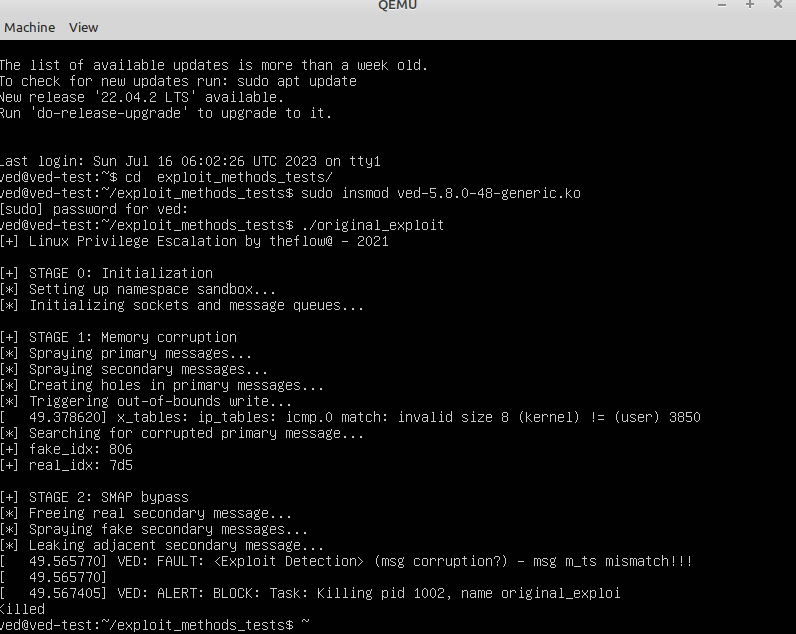
HardenedVault uses CVE-2021-22555 for testing because its public PoC/exploits cover both typical and non-mainstream exploit methods. Specifically, three exploits with different exploit methods were written based on CVE-2021-22555. VED’s defense target is not a specific vulnerability, but exploit methods. The three exploits for CVE-2021-22555 in this test image use the following exploit methods to achieve privilege escalation and container escape:
- Bypass SMAP (Supervisor Mode Access Prevention), which is a hardware-based security feature designed to prevent malicious code from accessing certain memory regions in the kernel
- KASLR/SMEP: Bypass KASLR (Kernel Address Space Layout Randomization) and SMEP (Supervisor Mode Execution Prevention)
- Infoleak
- Heap spray, which is a technique used in memory exploitation to allocate a large amount of memory in the heap and fill it with malicious code
- Kernel JOP (Jump-Oriented Programming) and ROP (Return-Oriented Programming), which are techniques used to hijack control flow in the kernel and execute arbitrary code
- Pipe primitive
- Cripple LKM (Linux Kernel Module) based security mechanism
Test image information:
- QEMU
- Ubuntu 20.04 for x86_64
- user:ved
- password:hardening
| Download Image | Expiry date |
|---|---|
| Vault-Range Image I | Aug 13 2023 |
| Vault-Range Image II | Aug 15 2023 |
| Vault-Range Image III with Reptile Linux rootkit | Aug 25 2023 |
| Vault-Range Image IV with Reptile Linux rootkit | Apr 3 2024 |
btw: Please contact us if the URL is expired contact(at)hardenedvault.net
Download and extract the image, then boot it up:
# qemu-system-x86_64 -cpu host -smp cores=4 -m 8192 -hda ved-ubuntu2004.img --enable-kvm -net nic -net user,hostfwd=tcp::7788-:22
You can login in via SSH:
# ssh -p 7788 [email protected]
Load VED at first:
# cd exploit_methods_tests/
# sudo insmod ved-5.8.0-48-generic.ko
Build the 3 exploits:
# ./build.sh
# ls
build.sh exploit.c original_exploit pipeprimitive.c ved-5.8.0-48-generic.ko
bypass_tetragon_exploit exploit_mod.c pipe_exploit readme.md writeup.md
Then you get 3 exploits:original_exploit, bypass_tetragon_exploit, pipe_exploit. The testing process:
-
Without loading VED, execute one of them. If privilege escalation is successful, it is recommended to reboot before conducting other tests.
-
With VED loaded, execute any of the exploits. After execution, it is recommended to reboot before conducting other tests.
The methods used for these three vulnerability exploits are respectively as follows:
original_exploit: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
bypass_tetragon_exploit:
https://hardenedvault.net/zh-cn/blog/2022-05-25-vspp/
https://grsecurity.net/tetragone_a_lesson_in_security_fundamentals
pipe_exploit:
https://github.com/veritas501/pipe-primitive
VED versions
VED has three versions of the Linux kernel module implementation: 1) Open Source Edition (free but unstable and without advanced protection features) 2) VED-LTS (stable version based on the open source version) 3) Commercial Edition (with advanced protection features)
If you plan to use VED in a production environment, you can try the public cloud version, such as the Hardened Linux on AWS (which integrates VED-LTS):
https://aws.amazon.com/marketplace/pp/prodview-4nur74fayxeis
If you are interested in the advanced version of VED and plan to deploy it cloudless envirionment, please contact: contact(at)hardenedvault.net
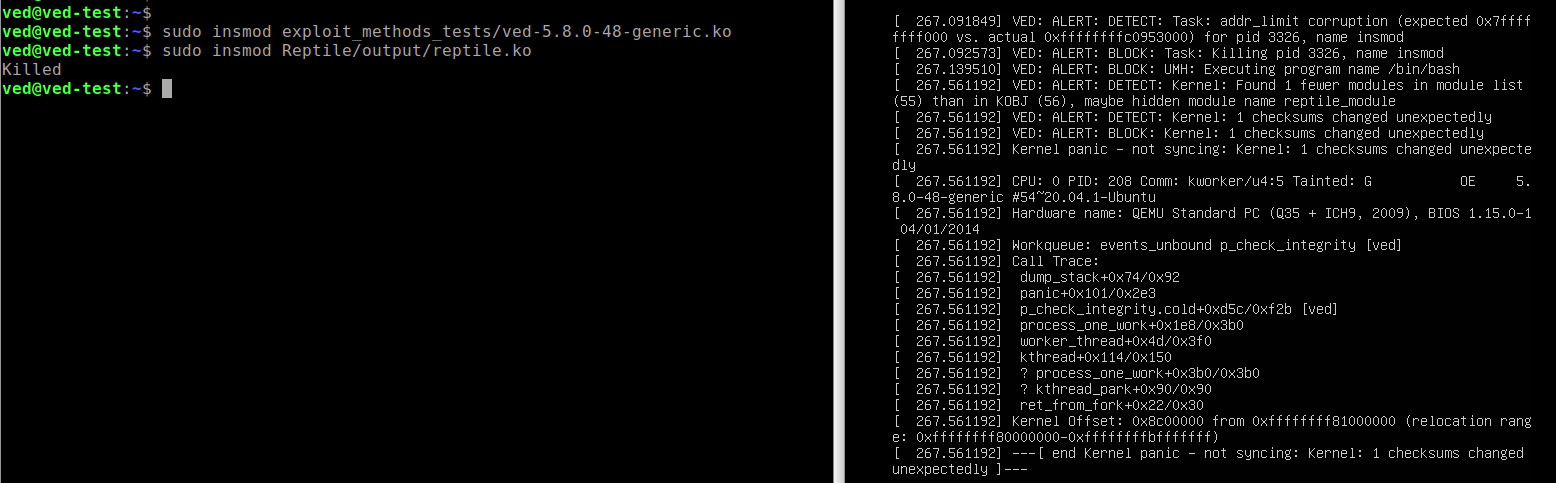
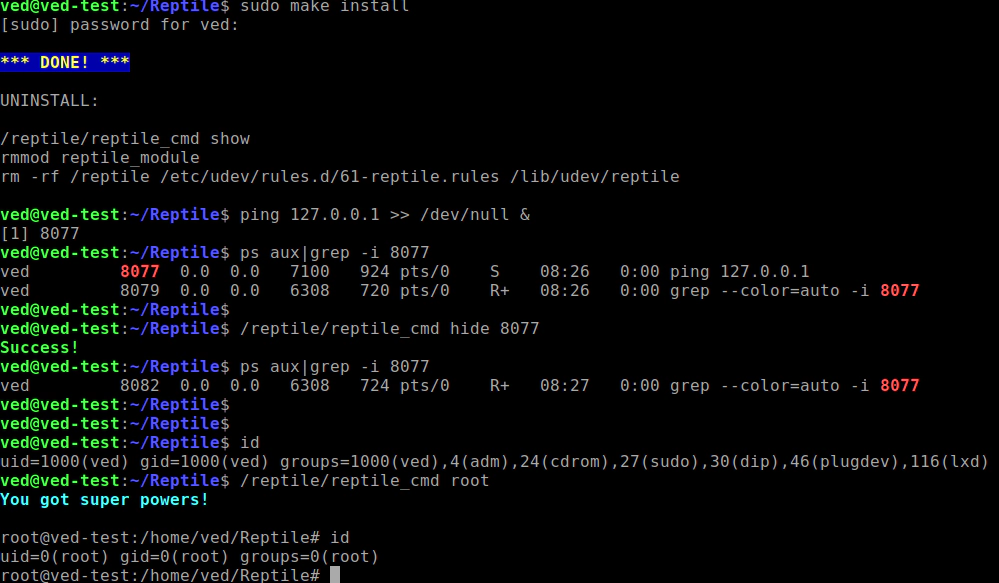
Linux kernel rootkit Reptile supports Linux 5.8 for Vault Range (Update: July 26 2023)
Some users told us that they couldn’t find a suitable rootkit to perform tests on the v5.8 kernel, so we’ve added Reptile support for the Linux kernel v5.8. Have a nice journey on post-exploitation playground!
Reptile can grants random users root privilege, hide process or network connections:
Rootkit detection and prevention: